Sadegh Sadeghi
Contact information
Assistant Professor at Department of Mathematics
Institute for Advanced Studies in Basic Sciences (IASBS), No. 444, Prof. Yousef Sobouti Blvd., Zanjan 45137-66731, Iran
s.sadeghi.khu@gmail.com, s.sadeghi@iasbs.ac.ir
Public key for PGP 16d55a935e4b8085d3d93477fdf30d89f220a621


About Me
Before joining Sharif University, I completed my PhD thesis on Automated Cryptanalysis of Lightweight
Symmetric Ciphers at Kharazmi University in 2019. Additionally, during my doctoral studies, I had
the opportunity to work as a visiting researcher at KU Leuven, collaborating with
Prof. Vincent Rijmen as part of the COSIC
research group.
Research Interests
News
more..
This paper evaluates a new ultra-lightweight RFID ownership transfer protocol (JIOT.2023.3267501). It finds the protocol vulnerable to a full Secret Disclosure: Exploiting weaknesses in its underlying permutation using l+1 sessions (where l is the secret length). Desynchronization Attacks, and previous owner compromising new owner's privacy. The analysis shows that inherent vulnerabilities in permutation functions can create weak points even in otherwise robust protocols. The attacks were practically demonstrated in a real-world setup using three Raspberry Pis and a wireless network, with steps detailed in a supplementary video.more..
This paper present a novel approach with MQTT authentication in securing industrial IoT.
more..
This paper demonstrates the critical importance of the internal structure of a permutation function in ensuring system security. This implies that even if a protocol is designed securely and efficiently, structural weaknesses in the function can render the protocol vulnerable. To illustrate this, we examine a recently published protocol named ULBRAP for supply chain management systems and reveal its security flaws, including secret disclosure and traceability attacks. We also demonstrate the attack step-by-step on Raspberry Pi devices, publishing the details on GitHub and presenting them in a video. The attack method requires 1,710,947 hash calculations, which takes approximately 5 min in our experiments. Finally, we propose a solution to address the issues associated with these functions.more..
LightSEC 2025 enthusiastically welcomes papers on algorithms, protocols, techniques, and their secure and efficient implementations for applications utilizing advanced cryptographic algorithms such as homomorphic encryption, zero-knowledge proofs, secure multi-party computation, cryptographic consensus protocols in blockchain applications, threshold cryptography, and post-quantum cryptography. The conference proceedings will be published in Springer-Verlag’s LNCS series. Submission website:http://www.easychair.org/conferences/?conf=lightsec2025
more..
In This paper, we propose a Secure and Efficient Lightweight Authentication Protocol (SELAP) to address ELWSCAS's security flaws. Using two Raspberry Pis, we measure SELAP's computation and communication costs, achieving 422 ms and 960 bits compared to ELWSCAS's 548 ms and 2048 bits. Simulations with NS3 further validate SELAP's performance, showing 276 successful authentications in 30 s, compared to ELWSCAS's 202, with 17% less delay. These results demonstrate SELAP's suitability for multi-sector IoT environments with varying conditions and high device density, delivering reliable performance.more..
In this work, we provide the first third-party analysis of the DBST cipher, challenging its security claims. The analysis reveals significant vulnerabilities within the cipher's structure, allowing the identification of distinguishers that can differentiate all 32 rounds of the cipher from a random permutation with a probability of one. This contradicts the designers' claim that the probability of a successful differential attack on any 32-round characteristic is bounded by $2^{-170}$. Additionally, the existence of differential distinguishers for the full round implies the existence of full-round impossible differential distinguishers, contradicting the designers' claim that the best impossible differential characteristic would require at most 6 rounds.This paper will be presented at the FSE 2024 in Leuven, Belgium.
more..
In this work, we have made significant advancements in our EUROCRYPT 2023 project (https://ia.cr/2022/1147) through three key improvements. Firstly, we have eliminated the need to determine the contradiction location in advance. Secondly, we have introduced a new bit-wise model that considers the internal structure of S-boxes. Lastly, we have introduced the CP model for the partial-sum technique for the first time. Applying our enhanced method to six different block ciphers has yielded impressive results. Some notable achievements include enhancing the integral distinguishers of QARMAv2-128 (QARMAv2-64) by 7 (5) rounds, improving ForkSKINNY integral distinguishers by 1 round, enhancing ForkSKINNY-64-192 ID distinguishers by 5 rounds, and improving integral key recovery on all SKINNY variants. Additionally, we have discovered numerous new ID/ZC distinguishers for Ascon, surpassing the speed of previous methods.
All news
more..
This paper has been published in the Eurocrypt-2023 conference. We introduced a unified method to fully automate three important cryptographic attacks on block ciphers. We invite you to explore our work here.
more..
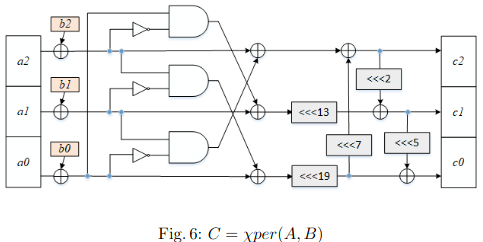
In this paper, we first introduce $\Xi$per, as a new hardware/software friendly component that can be implemented using bit-wise operations and extensively analyze its security. Next, we propose $\Xi$perbp, a lightweight authentication protocol based on $\Xi$per component. To evaluate the performance efficiency of our proposed scheme, we implement the $\Xi$perbp scheme on an FPGA module Xilinx Kintex-7 using the hardware description language VHDL. Our security and cost analysis of the proposed protocol shows that the proposed protocol provides desired security against various attacks, at a reasonable cost. Also, formal security evaluation using BAN logic and the Scyther tool indicates its security correctness. Besides, we analyze the security of a related protocol which has been recently proposed by Fan et al. It is a cloud-based lightweight mutual authentication protocol for RFID devices in an IoT system. The authors have claimed that their scheme is secure against active and passive attacks, however, our detailed security analysis in this paper demonstrates the major drawbacks of this protocol. More precisely, the proposed attack discloses the tag’s secrets efficiently. Given the tag’s secrets, any other attack will be trivial.
more..
In this paper, we propose a deterministic related key distinguisher for 31 rounds of the SFN. we are able to use the proposed related key distinguisher to attack the SFN in the known-plaintext scenario with the time complexity of $2^{60.58}$ encryptions. The data and memory complexity of those attacks are negligible. In addition, we will extend it to a practical chosen-plaintext-ciphertext key recovery attack on full SFN (32 rounds) with the complexity of $2^{20}$. We also experimentally verified this attack. Also, in the single key mode, we present a meet in the middle attack against the full rounds block cipher for which the time complexity is $2^{80}$ the SFN calculations and the memory complexity is $2^{35.6}$ bytes. The data complexity of this attack is only two known plaintext and their corresponding ciphertext.
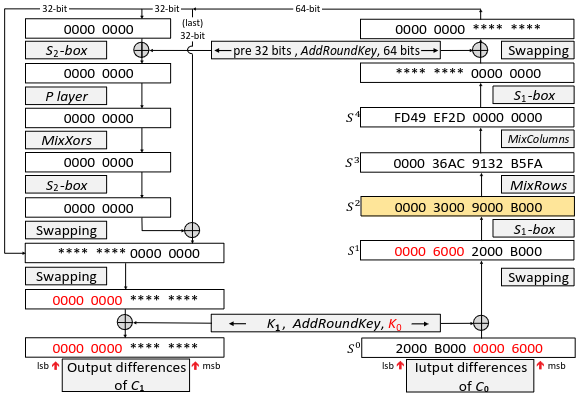
more..
In this paper, we introduce a framework to utilize Statistical Ineffective Fault Analysis (SIFA) in the persistent fault setting by proposing Statistical Ineffective Persistent Faults Analysis (SIPFA) that can be efficiently applied to Feistel ciphers in a variety of scenarios. To demonstrate the effectiveness of our technique, we apply SIFPA on three widely used Feistel schemes, DES, 3DES, and Camellia. Our analysis reveals that the secret key of these block ciphers can be extracted with a complexity of at most 250 utilizing a single unknown fault. Furthermore, we demonstrate that the secret can be recovered in a fraction of a second by increasing the adversary’s control over the injected faults. To evaluate SIPFA in a variety of scenarios, we conducted both simulations and real experiments utilizing electromagnetic fault injection on DES and 3DES.

more..
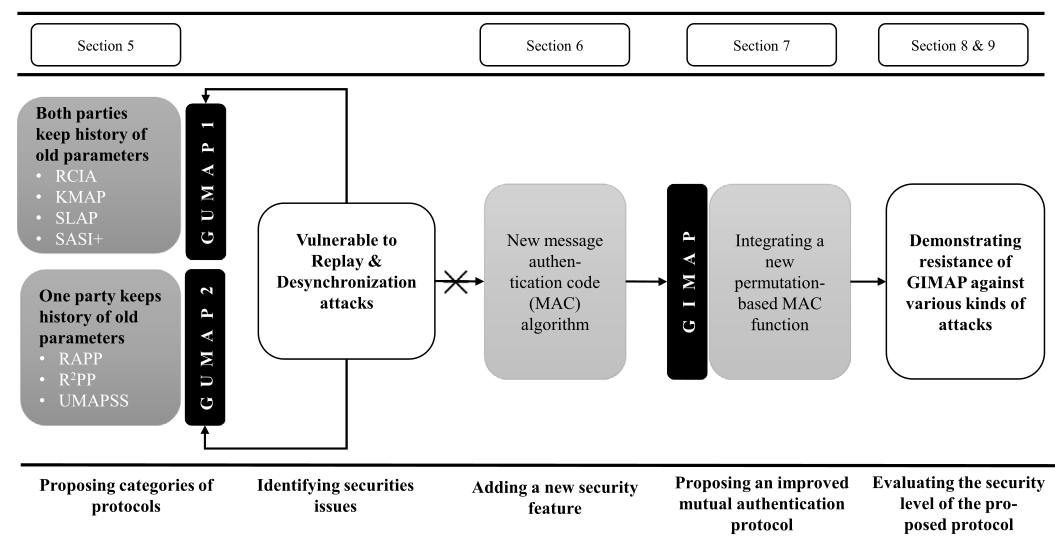
In this project, we evaluate the security level of recent ultra-lightweight mutual authentication protocols and show their susceptibility to replay and desynchronization attacks. We also show that these protocols can be grouped into a generalized version of ultra-lightweight mutual authentication protocols (GUMAPs) and classify them into two categories. We then establish that both groups are vulnerable to replay and desynchronization attacks. To eliminate these vulnerabilities, we present a new message authentication code (MAC) function to propose a more secure generalized improved mutual authentication protocol (GIMAP).